Aug 25, 2025
Workday Breach Joins a Growing Wave: Why the Second Half of 2025 is a Hacker’s Playground
The Workday breach is yet another reminder: the breach curve is rising, and the stakes are accelerating. Here's how to stay ahead.
Aug 25, 2025
The Workday breach is yet another reminder: the breach curve is rising, and the stakes are accelerating. Here's how to stay ahead.

It’s been a brutal summer for SaaS companies.
The Workday breach is just the latest headline. Before that, it was Google, then Cisco, Allianz Life, and Qantas. And summer isn't even over yet.
This latest wave of breaches usually starts with a phone call. A voice that sounds like IT, HR, or a trusted vendor. By the end of the day, customer data is quietly walking out the door. No zero-days. No sophisticated malware. No brute-force network exploit. Just people, trust, and SaaS.
The second half of 2025 is proving to be the most dangerous stretch of the year for exactly this reason. Five different companies in five different industries, but the story is starting to sound eerily familiar: attackers aren’t breaching hardened infrastructure; they’re bypassing it entirely by exploiting human trust and SaaS connectivity.
It’s not just anecdotal; there are measurable signals that attack activity climbs as the year winds down. In Q3 2024, organizations saw a 75% year-over-year increase in cyberattack volume, averaging 1,876 attacks per week, making the closing months feel like constant combat. Similarly, in Australia, data breach reports jumped 25 % in the second half of 2024 compared to the first half, with more than 50% of incidents recorded in that window alone. There’s a familiar rhythm that makes the end of the year the most dangerous stretch.
By midyear, researchers were already flagging the cyber attack trends. Unit 42 reported that social engineering now plays a role in over a third of major intrusions. In the second half, pressure mounts inside organizations: annual targets, budget deadlines, performance cycles. Security controls get easier to sidestep when everyone’s in a hurry or stressed, and attackers know it. That’s when the phishing emails spike, the vishing calls come harder, and malicious OAuth requests slip by more easily.
Take Allianz Life. Attackers impersonated IT support and convinced staff to install what looked like a routine Salesforce Data Loader update. It wasn’t. Within hours, CRM data was quietly siphoned off. Qantas saw something similar: a third-party contact center was compromised through spoofed calls and SIM-swapping tactics, ultimately exposing records for 5.7 million travelers. Google wasn’t immune either. ShinyHunters, the same group suspected in multiple Salesforce-related incidents, used malicious OAuth apps to compromise a corporate CRM instance and exfiltrate business contact data before anyone noticed.
And now there’s Workday. Attackers targeted employees with a blend of voice phishing and SMS-based lures, tricking them into onboarding malicious OAuth apps or approving large-scale data exports. The breach didn’t touch customer tenants directly, but it’s part of the same campaign and a coordinated wave focused on SaaS applications and the people who use them.
Different companies. Different defenses. Same outcome. SaaS became the breach path.
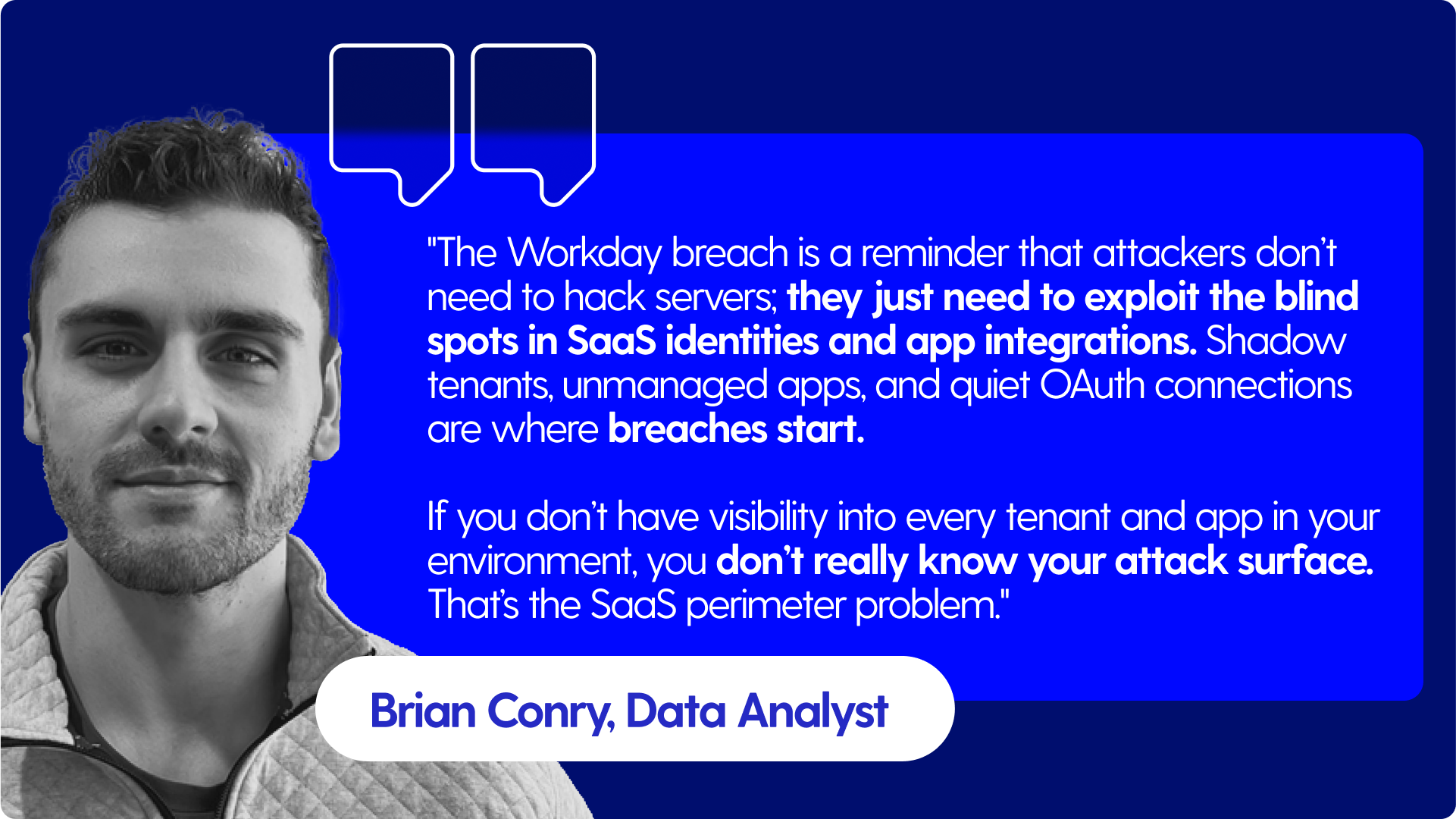
What ties these incidents together isn’t just the attackers’ persistence but their precision. They’ve learned where modern trust lives: in the invisible connections between SaaS tools, access, and identities. OAuth tokens and app-to-app integrations aren’t vulnerabilities in the traditional sense. They’re productivity hacks and staff conveniences, and attackers are weaponizing them.
Many organizations can’t produce a complete inventory of SaaS apps in use, let alone track which ones have access to sensitive data. Unmanaged SaaS, rogue tenants, and overlooked integrations create blind spots — and attackers thrive in the dark.
While none of these breaches have been tied to missing MFA controls, the pattern highlights why every SaaS app connected to your ecosystem should have MFA enabled and enforced. Employees must understand the risks of bypassing it, whether intentionally or not. Attackers know that’s where human behavior and technology diverge, and they exploit that friction relentlessly.
Attackers gain access through social engineering tactics, then move laterally through unmanaged SaaS and connected apps. Your SaaS perimeter isn’t defined by your own network anymore; it extends across every integrated app, tenant, and authorized connection your employees use daily.
From the Google, Cisco, Allianz Life, Qantas, and now Workday breaches, one thing about the second half of 2025 is painfully clear: SaaS has become the quickest route to compromise — and trust is the lever attackers are pulling hardest. Defending against this wave isn’t about more dashboards or noisy alerts; it’s about deep visibility into your SaaS ecosystem and responding instantly when user or app behaviors fall outside the norm. Knowing which SaaS apps are connected, what permissions they’ve been granted, and when something starts behaving unexpectedly has become critical. Real-time visibility into OAuth consent activity and the ability to surface rogue integrations before data moves can make all the difference. Equipping employees with the context to pause — even briefly — when “IT” or “HR” calls with an urgent request is increasingly part of the defense.
The Workday breach isn’t an isolated event; it’s another warning shot in a broader campaign aimed squarely at SaaS ecosystems. The question isn’t whether attackers will probe your perimeter — they already are. The real challenge is spotting and shutting them down before access turns into compromise.

Thwarting the breach curve takes more than knowing what’s out there; it requires the ability to act on what you see. That starts with uncovering every SaaS app — managed or unmanaged — and understanding who has access, what permissions they’ve granted, and access behaviors over time. The difference comes from being able to respond immediately when something deviates from the norm, before it becomes a data loss event.
That’s exactly where Grip Security comes in. Grip gives security teams continuous, unified visibility across all SaaS apps, identities, and connections — including shadow tenants and unmanaged apps hiding outside SSO. By mapping the full SaaS ecosystem and monitoring OAuth behaviors in real time, Grip empowers defenders to:
The second half of the year is always noisy. Deadlines stack up. Alerts multiply. Attackers know it and they thrive in the chaos. Grip helps teams cut through that noise by showing where SaaS risks live, which behaviors are suspicious, and when to act.
The Workday breach is yet another reminder: the breach curve is rising, and the stakes are accelerating. The challenge is staying ahead of it. Grip makes it possible, revealing every SaaS connection, exposing identity risks, and enabling action before compromise happens. Book time with our team to see how Grip can help you thwart the breach curve.
10 SaaS Security Risks Most Organizations Miss
Free Guide: Getting Started with Identity Threat Detection & Response (ITDR)


Compliance & Governance
Risk Management

Operational Efficiency
Risk Management





