Expand the reach of your IGA solutions and onboard new SaaS apps without connectors.
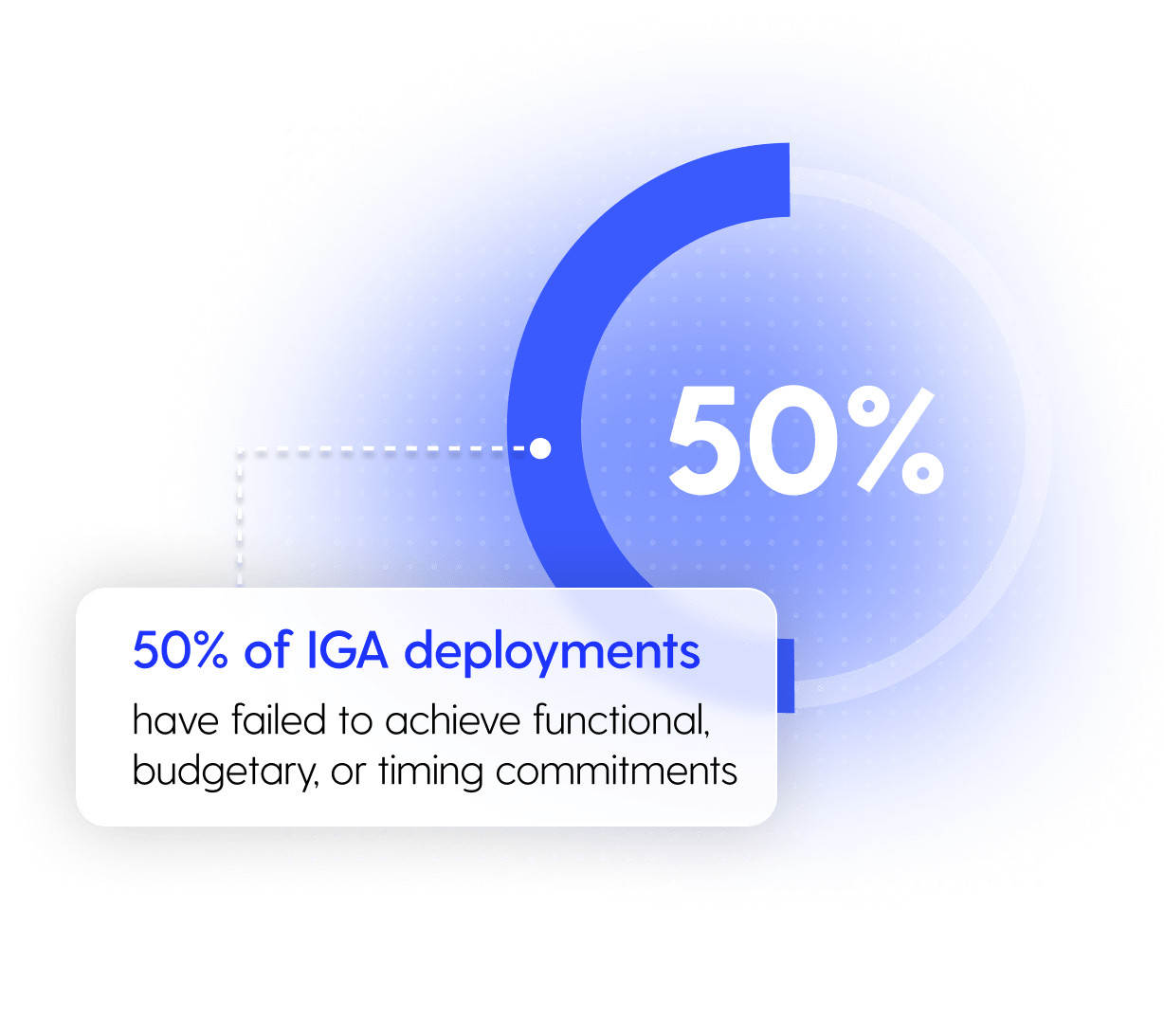
Grip connects with your IGA solution out of the box. No heavy lifting. No code. No waiting. Once integrated, your IGA can:
It’s SaaS governance made simple, at enterprise scale.
Book a Demo
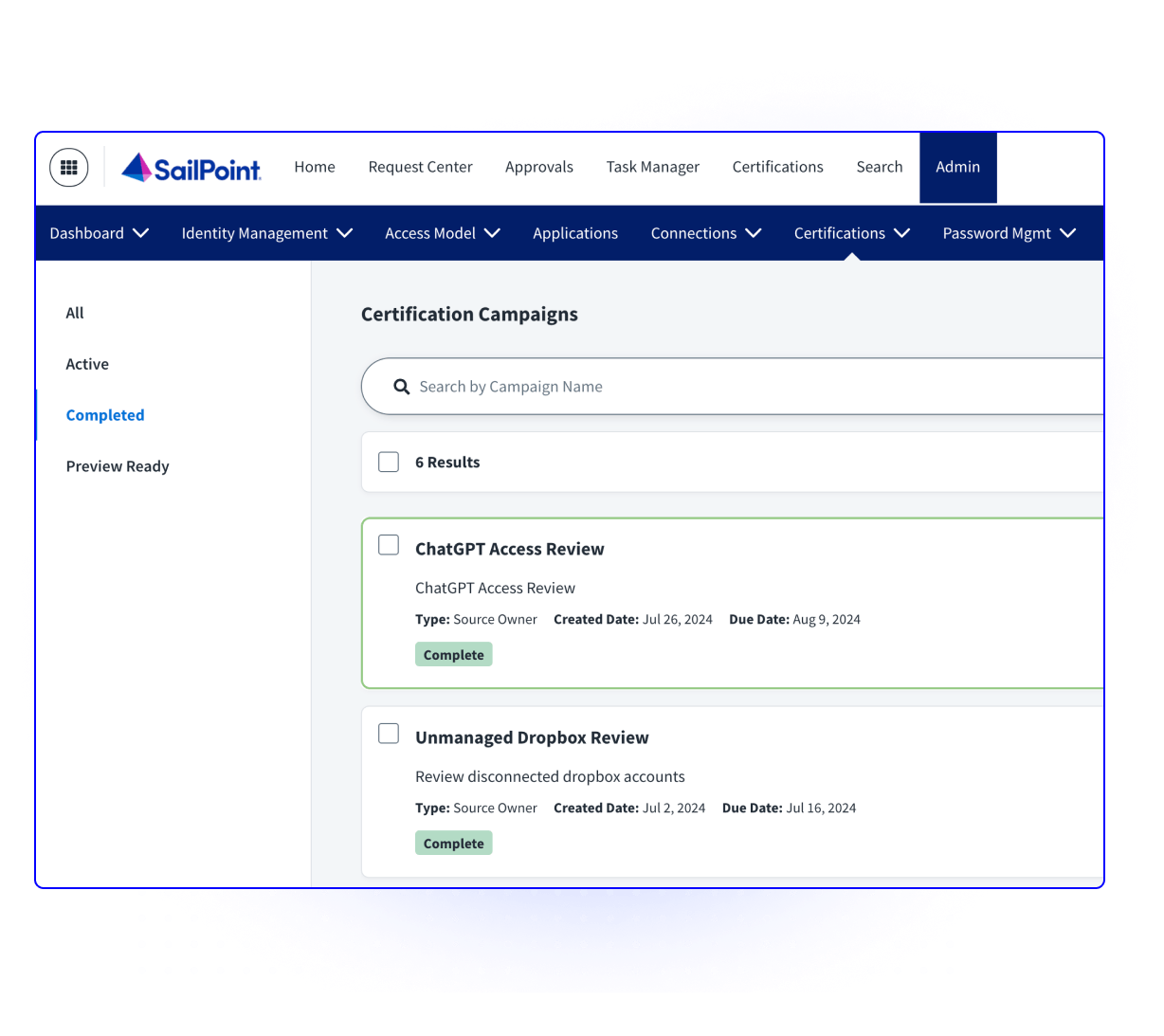
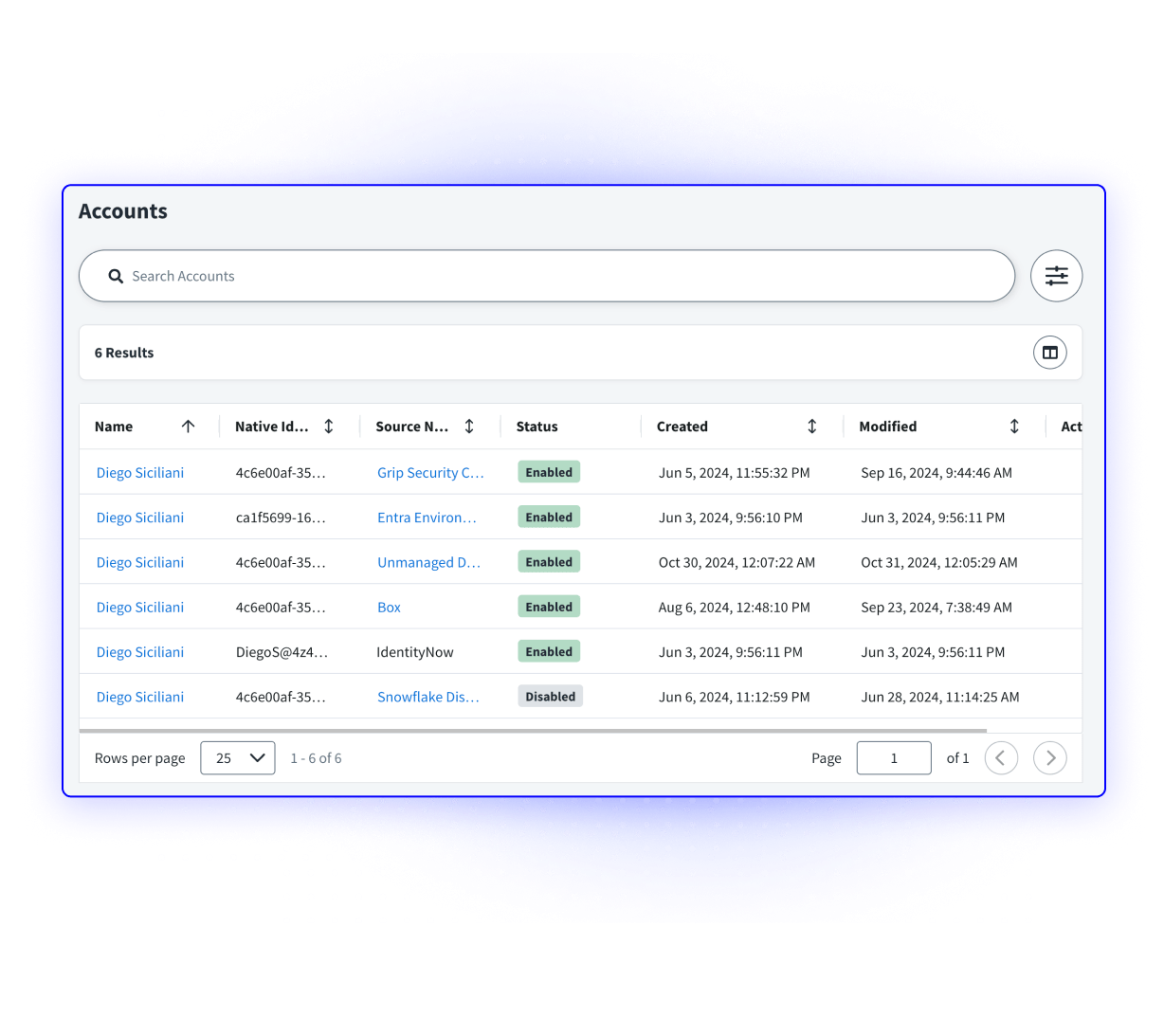

Grip enables your Identity Governance and Administration (IGA) platform to discover and govern SaaS apps, including shadow SaaS, without the need for custom connectors. With Grip, organizations gain instant visibility into SaaS usage and can quickly onboard apps into their IGA solution, reducing the time and effort required for integration.

Yes. Grip works seamlessly with leading IGA platforms to extend their governance reach. Once integrated, your IGA can certify access with the right business owners and revoke access to SaaS apps discovered by Grip, even if those apps aren’t natively connected to your IGA.

Grip discovers and helps govern all types of SaaS applications: managed apps, unmanaged shadow SaaS, GenAI apps, and personal-use apps. This ensures comprehensive SaaS visibility across your organization and eliminates governance blind spots.

Grip identifies potential app owners and power users to ensure the right people review access. It also enriches certification workflows with critical context, including user associations and app risk scores. Your IGA can then leverage this data to confidently certify access to shadow and unmanaged SaaS apps—no more overlooked apps or approvals.

Absolutely. Whether it’s post-certification or part of user offboarding, your IGA can call Grip to revoke access to unconnected SaaS apps. Grip uses password rotation via robotic process automation (RPA) to securely revoke access—no API, no connector, no complexity.